The Rise of the Data Product Manager: Bridging Business and Analytics

Why Data Product Management Is the Role to Watch in 2025 Data is no longer just a supporting function—it’s now at the core of how businesses make decisions, design products, and compete in the market. As organizations race to become more data-driven, a new role has emerged in the spotlight: the Data Product Manager (DPM). ...
Read moreHow Data Compliance Solutions Can Prevent Data Breaches

Data breaches have become a growing concern for businesses and individuals in an increasingly interconnected world. The consequences of these breaches can be far-reaching, including financial loss, damage to reputation, and compromised personal information. However, organizations can greatly reduce the risk of data breaches with the right data compliance solutions. This post explores the importance ...
Read moreWhat Are the Benefits of Custom Web Development for Companies?

A strong online presence is crucial for businesses looking to thrive and stay competitive. Custom web development offers tailored solutions that address the unique needs of a company, differentiating it from competitors who rely on generic platforms. By investing in custom web applications, businesses can enhance user experience, improve functionality, and foster brand loyalty. This ...
Read moreCommon Malware Attacks and How to Avoid Them

Introduction In 2025, malware attacks have reached unprecedented levels, affecting not only large corporations but also small businesses, government agencies, and individual users. Cybercriminals are leveraging advanced tactics such as artificial intelligence, automation, and sophisticated evasion techniques to bypass traditional defenses. The financial impact is staggering, with global ransomware losses alone projected to surpass billions ...
Read moreWhat Is the Difference Between Qvidian and Loopio?

Qvidian and Loopio are popular proposal management platforms that help businesses streamline their response process. While they share similar goals, such as improving efficiency and collaboration during proposal creation, each offers unique features and tools that set them apart. Below, we will explore the key differences between Qvidian and Loopio—keep reading to learn which platform ...
Read moreStay a Step Ahead: How True Regional Visibility Creates an Impenetrable Defense Against Localized Fraud

Have you ever wondered how fraudsters bypass security systems that appear to be impenetrable? The secret is localization. The cybercriminals of today are not trying to reach a large audience of users; they act as regional users with devastating precision. When these threats can be real-looking logins or payment fraud, it is easy to see ...
Read moreSattelitter: What They Are, How They Work & Why They Matter

Quick answer A sattelitt (Norwegian spelling for “satellite”) is a man-made object placed into orbit around Earth or other celestial bodies. It serves various functions like communication, navigation, Earth observation, and scientific research. Most sattelitter use solar power, onboard thrusters, and transponders to operate in space efficiently. What Are Sattelitter and Why Do They Matter? ...
Read moreZero Touch Deployment: The Final Frontier for IoT at Scale

Imagine unboxing 5,000 industrial sensors. Each one needs to be configured, authenticated, connected, and verified before it can be deployed in the field. Now multiply that across ten warehouse locations, 20 trucks per facility, 12 access points per site, and a ticking project deadline. Your engineering team? Already underwater. This is where the dream of ...
Read moreHow SD-WAN Simplifies Multi-Location Network Management
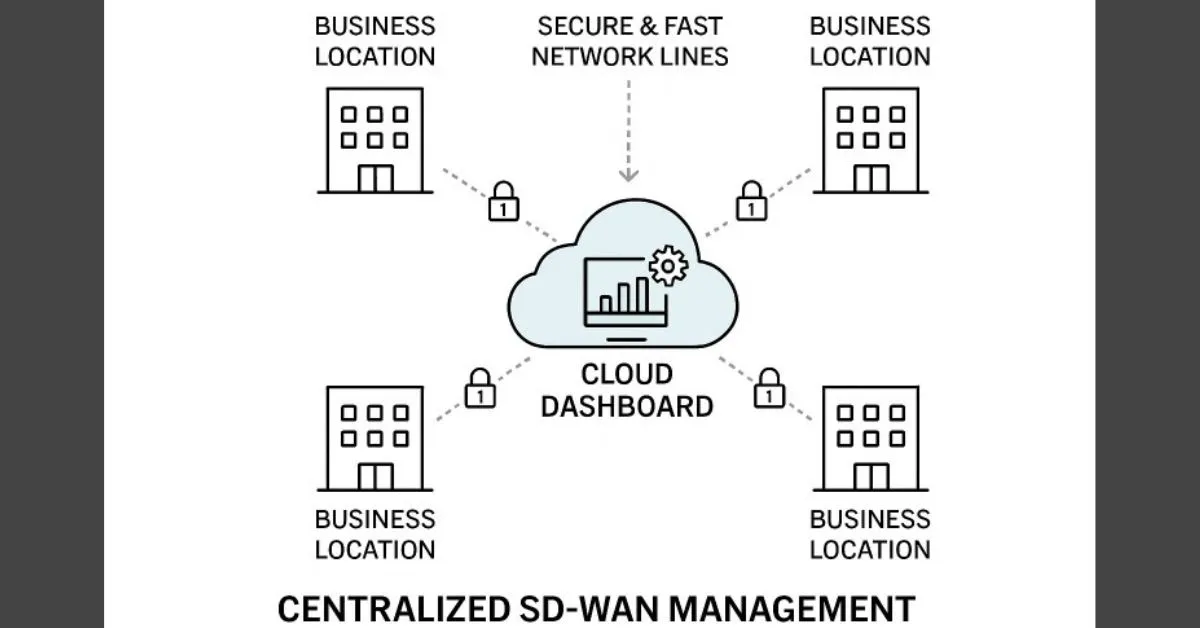
Key Takeaways Managing network connectivity across multiple offices, branches, or locations has historically posed a daunting challenge for many organizations. The need to maintain seamless connections, manage security, and coordinate changes across dispersed sites often resulted in ballooning costs and technical headaches. Manual configurations, limited visibility, and isolated troubleshooting processes were the norm. However, the ...
Read moreFrom Prompts to Models: How Generative AI Actually Works
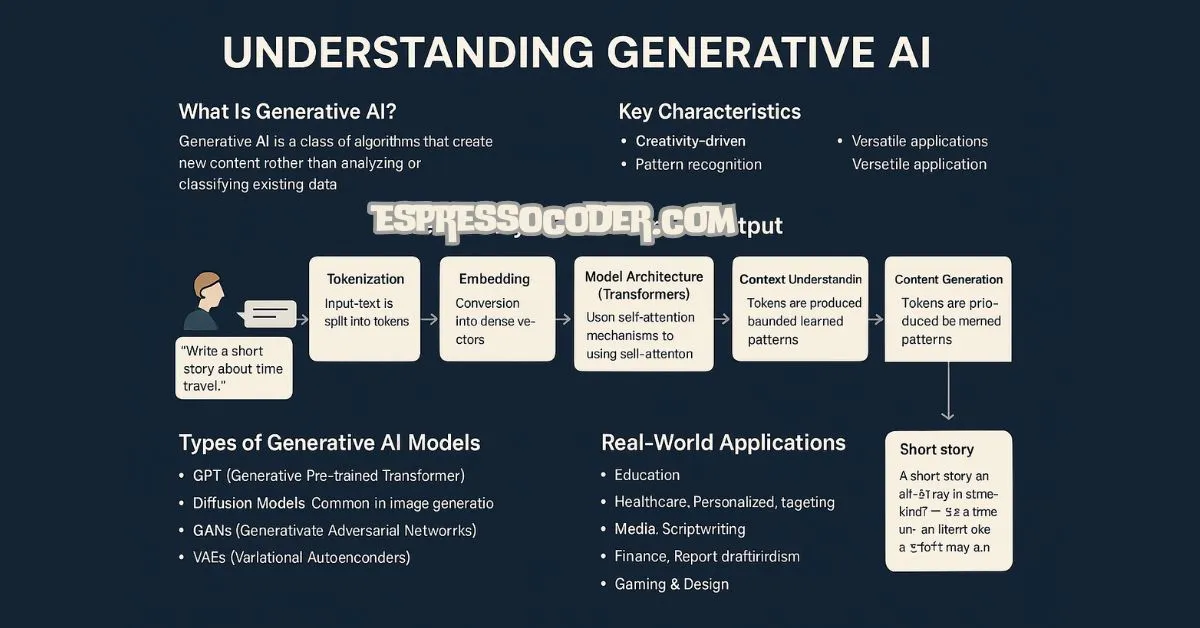
Generative AI has rapidly transformed how humans interact with machines. Fromproducing entire essays to generating photorealistic images or functional code, thistechnology is redefining creativity, productivity, and automation. What sets it apart is itsability to produce new content rather than merely process existing data. As industriesadapt to this new paradigm, the curiosity around how generative AI ...
Read more